Other than regularly scanning your credit card statements, you'll want to put in place text or e mail alerts to inform you about specific forms of transactions – like anytime a order around a longtime amount pops up within your account.
Use contactless payments: Go for contactless payment procedures as well as if You need to use an EVM or magnetic stripe card, ensure you deal with the keypad with your hand (when entering your PIN at ATMs or POS terminals) to circumvent concealed cameras from capturing your facts.
Cloned credit cards sound like one thing away from science fiction, However they’re an actual risk to buyers.
Que ce soit lors d’un retrait au distributeur, d’un paiement dans un magasin ou d’un achat en ligne, les utilisateurs peuvent facilement se faire piéger.
Financial ServicesSafeguard your customers from fraud at each and every action, from onboarding to transaction checking
Dans cet posting, nous allons vous expliquer ce qu’est une carte clone, comment elle est fabriquée, comment retrouver la personne qui a piraté votre carte bleue, les condamnations pour utilisation frauduleuse de carte bancaire et remark se faire rembourser d’un faux internet site. Qu’est-ce qu’une carte clone ?
Pour éviter les arnaques lors de l'achat d'une copyright, il est essentiel de suivre certaines précautions :
To not be stopped when requested for identification, some credit card burglars place their unique names (or names from a phony ID) on the new, fake cards so their ID and also the name on the card will match.
Find out more about how HyperVerge can safeguard from card cloning at HyperVerge fraud prevention methods.
Stealing credit card data. Intruders steal your credit card information: your identify, along with the credit card variety and expiration day. Frequently, robbers use skimming or shimming to acquire this information.
In the same way, shimming steals info from chip-enabled credit cards. In keeping with credit bureau Experian, shimming functions by inserting a thin unit often known as a shim right into a slot with a card reader that accepts chip-enabled playing cards.
Comme des criminels peuvent avoir set upé des micro-caméras près du comptoir dans le but de capturer le code key de votre carte, couvrez le clavier où vous saisissez votre code PIN avec votre clone carte autre most important. Choisissez des distributeurs automatiques fiables
La copie des données de la piste magnétique s'effectue sans compromettre le bon fonctionnement de la carte bancaire.
When fraudsters get stolen card data, they will at times utilize it for tiny buys to check its validity. Once the card is confirmed valid, fraudsters by yourself the cardboard to make greater buys.
 Mara Wilson Then & Now!
Mara Wilson Then & Now! Jennifer Love Hewitt Then & Now!
Jennifer Love Hewitt Then & Now! Danielle Fishel Then & Now!
Danielle Fishel Then & Now!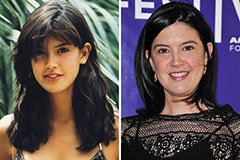 Phoebe Cates Then & Now!
Phoebe Cates Then & Now! Peter Billingsley Then & Now!
Peter Billingsley Then & Now!